Welcome to the next generation of cybersecurity analytics
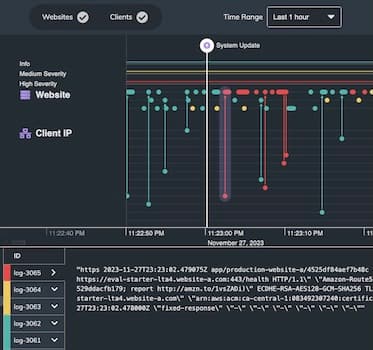
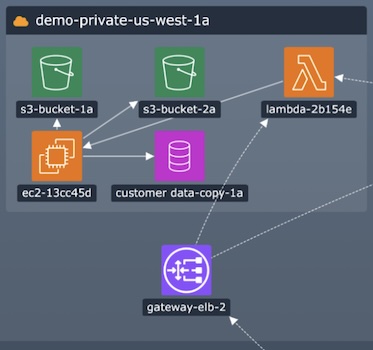
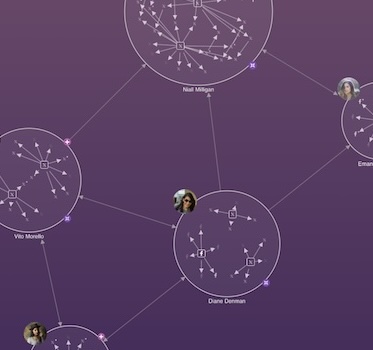
Learn how Cyberflow Analytics have used our network visualization functionality to develop the next generation of cyber threat intelligence platform – built for the scope and scale of the Internet of Things. Suitable for a technical and non-technical audience.