As companies move their digital infrastructure to the cloud, and as Infrastructure as a Service (IaaS) becomes the norm, the cybersecurity challenge is more complex than ever. Complex cloud infrastructure presents a wealth of opportunity for unintentional misconfiguration, leaving organizations open to malicious attacks, or non-compliance with data protection laws.
Cybersecurity software vendors need to understand these specific risks in an ever-changing cyber threat landscape.

I’ve written a cloud security visualization white paper for anyone in the cybersecurity industry who needs to understand the challenge of keeping cloud assets secure. If you’re building applications to help organizations combat cyber threats across their networks, you’ll discover why data visualization belongs on your roadmap.
Why visualize cloud security?
The main problem with cloud security is visibility. It’s impossible to protect assets when you don’t know what assets you have, or how they are connected. Everything from storage and computing to networking and access control is virtualized and abstracted to a collection of settings on a cloud management console.
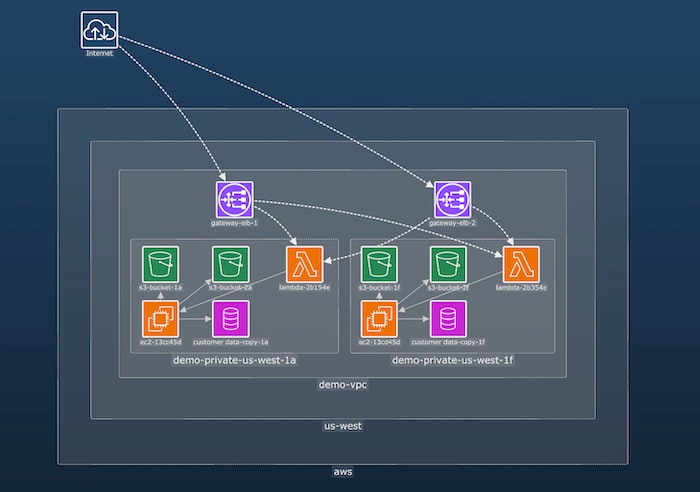
Two of the most powerful visual representations of cloud security are networks and timelines. The white paper gives detailed examples of why they’re so valuable, and how cybersecurity software vendors can leverage them to bring situational awareness and actionable insights to their customers.
Use cases for cloud security visualization
The white paper includes fictitious cloud security examples based on real-world scenarios of posture management and compliance, attack path visualization, detection and response timelines, an investigation using the MITRE ATT&CK framework, and network traffic monitoring.
Analyzing attack paths in network visualizations
In our attack path visualization use case, you’ll see how a user interacts with a fired alert in the cloud network to quickly detect and reveal the critical asset responsible: a misconfigured S3 bucket.
The visualization filters out unaffected parts of the network and then rearranges the attack path in sequence, adding useful annotations for context. In a busy, complex cloud network, identifying attack paths in isolation is an essential technique.
Investigating the timeline of malicious activity
The report also explains how timeline analysis speeds up incident detection and response.
A timeline visualization of a hybrid cloud infrastructure provides a rich history of the events that led to malicious activity. First we explore a high level heatmap to achieve situational awareness. Then we drill down into the sequence of individual alerts that tell us exactly what happened.
Download your free cloud security guide
The key to understanding cloud security posture, mitigating risks, and detecting and responding to threats lies in the ability to easily communicate the threat landscape. This guide shows how interactive visualizations, such as graph and timeline views, are essential to this communication process.
Download it today and start to prioritize more effective cloud security management in your cybersecurity application.



