Smarter cyber threat intelligence visualization
As the volume and complexity of cyber security data grows, our ability to understand it diminishes. This webinar explains how you can use a combination of advanced graph technologies to carry out better cyber threat intelligence visualization analysis.
The session showcases two technologies that help make complex analysis tasks easier: KeyLines and EclecticIQ.
Why cyber threat intelligence visualization is essential

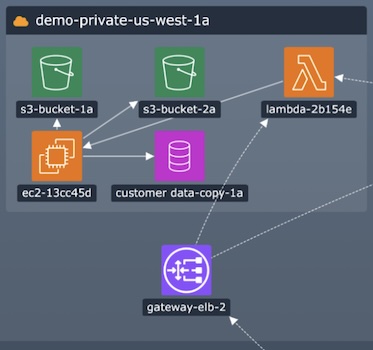
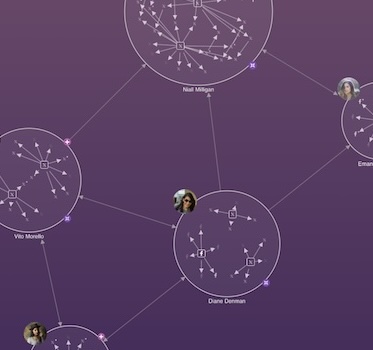
This session is useful to anyone working in the cybersecurity industry who is keen to learn more about the important part graphs play in understanding cyber threat intelligence. Cambridge Intelligence’s Chief Product Evangelist Corey Lanum demonstrates the power of graphs, and why visualizing connected data is the best way to understand your complex cyber intelligence data. That could include IP communications, network devices, malware propagation, insider threats, STIX and TAXII data.
The webinar is co-presented by Aukjan van Belkum, Technical Product Manager at EclecticIQ. His 15 years of experience working with cybersecurity products have given him a unique perspective. Having worked closely with threat researchers and threat analysts, he’s well placed to recommend the best strategies for fending off cyber attacks.
Aukjan demonstrates the EclecticIQ Platform, a collaborative platform for collecting, analyzing and visualizing STIX and TAXII data from many different sources. If you want to find out how to boost the effectiveness of your threat intelligence practices and operations, this video is for you.