In this article, we’ll see how Core4ce’s cyber forensics platform, Cyberscape, uses KeyLines to help keep critical systems safe.
Cyber threat intelligence as a government priority
Just over two years ago, in May 2021, President Biden signed Executive Order 14028: improving the nation’s cybersecurity. Just two days before, he had declared a state of emergency following a ransomware attack on the Colonial Pipeline, blocking the flow of fuel in the US.
These two events highlighted the scale, scope and sophistication of the cyber threats facing governments. State actors, hacking groups and organized criminal gangs are increasingly targeting critical infrastructure, compromising the systems that keep countries functioning.
It’s not just federal systems at risk. Attacks like the one on the Colonial Pipeline show the challenges of supply chain and critical infrastructure security. Hackers can take down national assets, especially if they’re publicly owned, without touching a federal network.
It’s no surprise, then, that two of EO-14028’s priorities were to improve information sharing between government and industry, and to more effectively join the dots between attacks and attackers.
That’s exactly what Core4ce’s Cyberscape platform does.
Core4ce Cyberscape: unmasking cyber threats
Since 2018, Core4ce’s team of data scientists, engineers, and cyber experts has helped the US federal government solve complex challenges with data. As a prime contract holder across multiple projects, they build systems that improve government operations, data analytics and engineering.
Cyberscape, their latest product, simplifies the cyber forensics process, helping agencies and financial institutions understand threats and unmask the actors behind them in a uniquely collaborative way.
Using a combination of data enrichment and visual investigation techniques, analysts build a picture of their attacks and adversaries in a unified graph visualization chart – powered by KeyLines, our JavaScript graph visualization toolkit.
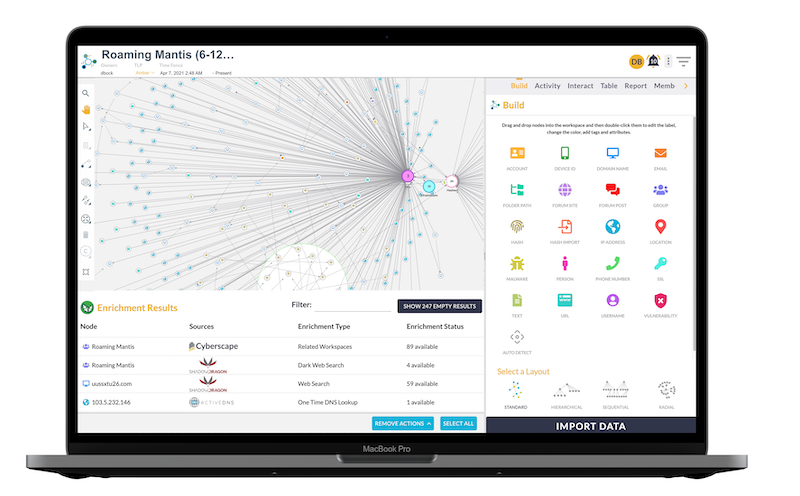
Let’s take a closer look.
Know your enemy: who’s rattling the doors and windows?
Dave Bock, VP of Strategy, explained the purpose of Cyberscape:
“Governments and businesses face threats from all directions. Despite efforts to secure systems to keep adversaries out, breaches and unauthorized access are inevitable.
“Cyberscape isn’t about locking down systems or monitoring networks. Instead, we help organizations see who’s rattling their doors and windows. We help to forensically piece together disparate information, connecting events and digital trails to reveal the bigger threat picture.”
An investigation begins with a workspace. Here, analysts can start from scratch or pick up an existing investigation by another team looking at the same actors.
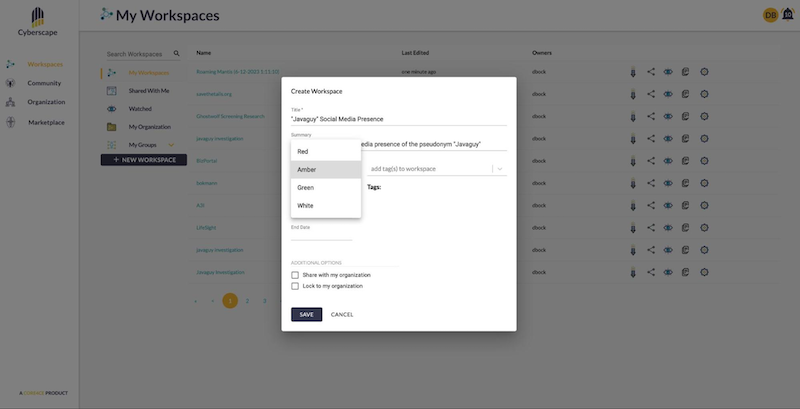
Using a drag-and-drop interface, analysts add seed nodes representing the entities they need to better understand. They could be IP addresses, email addresses, known aliases, device IDs or Malware signatures. These form the starting point for their investigation.
Analysts can also add rich text annotations, tags, risk scores and custom styling to their nodes to help tell the story, and make the charts more informative:
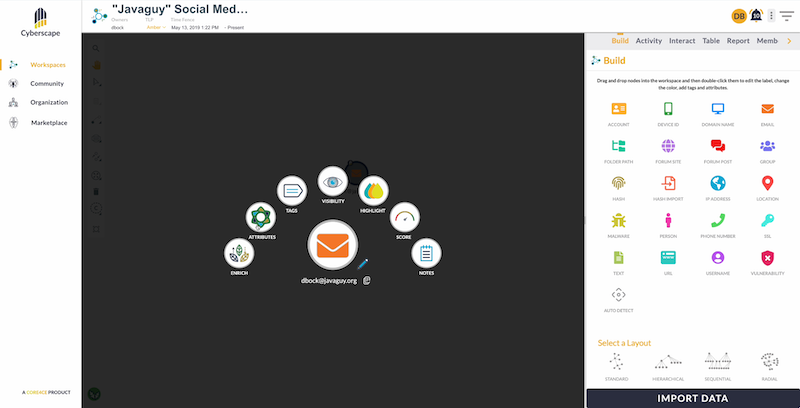
Next, things get really smart.
Bridging data silos
Once we have our seed nodes on the chart, we start enriching them.
Cyberscape allows analysts to enrich their data from a huge range of sources, including internal databases and an ecosystem of data providers covering OSINT, the dark web and proprietary threat intelligence feeds.
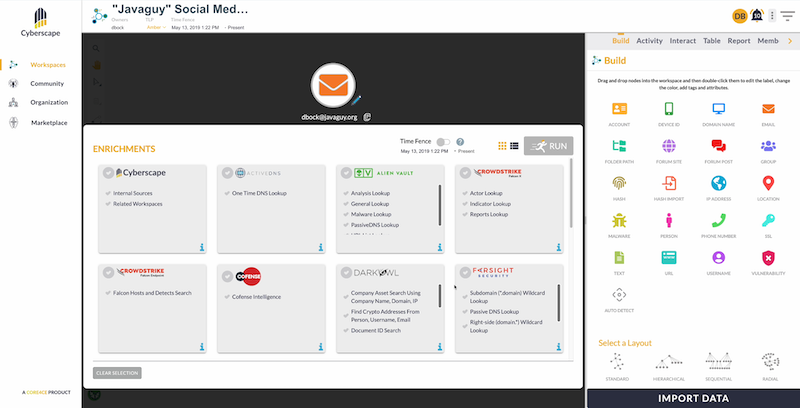
With this information in a single place, a picture starts to form. KeyLines nodes represent entities, and the connections between them are shown as annotated links:
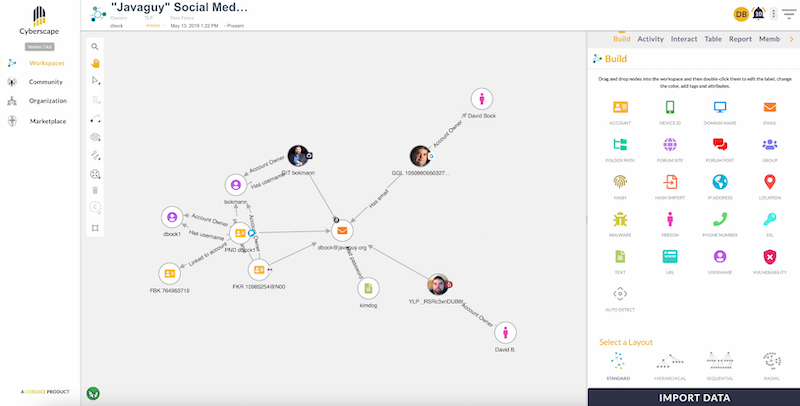
Charts can quickly get pretty busy, so Cyberscape’s developers have incorporated some smart KeyLines functionality to help remove the noise.
It’s easy to group nodes if multiple sources have returned duplicated or related information:
Or filter and delete nodes we’re not currently interested in:
KeyLines’ automatic graph layouts also help detangle complex charts, laying out nodes in a clear and insightful way:
Dave Bock explains the role of the graph:
With any complex investigation, it’s easy to get overwhelmed with information. You have multiple analysts, incidents, data sources and parallel investigations going on. Keeping track of everything is impossible without the right tools.
KeyLines lets our customers scale-up their investigations. They can collaboratively build visual “murderboards” of their adversaries, connecting events with accounts, and accounts with real identities and motives. Instead of pinning paper and bits of string to a wall, they can pull data from practically any source into a single interactive view.
Cyberscape creates one holistic view across all of these data sources, combining into one visualization not possible with one data source alone.”
Easy intelligence sharing
Intelligence is useless until it’s shared with the right people. In government cyber security circles, multiple agencies often collaborate on individual threats. In fact, US national cyber defense is jointly owned by the Department of Defense and the Department of Homeland Security.
That’s why the final step of the intelligence cycle is so important: dissemination.
Cyberscape lets analysts export high-resolution custom PDF reports. These can be quickly created and shared with whoever needs them.

Alternatively, charts can be saved and shared as active, or finished, investigations. This allows analysts to easily pick up relevant results from previous projects to help inform new ones. The result? Joined-up, effective investigations that reveal insights needed to make critical policy decisions faster.
What’s next?
The Core4ce team has big plans for Cyberscape’s future. There are still multiple advanced social network analysis and visualization features to uncover insight in disparate threat datasets. David Bock explained:
“Our goal is to give analysts a complete view of their adversaries. We’ve built an ecosystem of data suppliers, pulling billions of data points into a single platform. When they connect all that data in KeyLines, there’s really no limit to what’s possible.
We have plans for timelines, geospatial views, pathfinding and centrality algorithms: together they’ll reveal the full picture that analysts need to see. The cyber threat is huge, and growing, but Cyberscape will help organizations fight back.”
Want to try Cyberscape for yourself? Visit the website to learn more.



